Setup SFTP on a dedicated port.
Using a dedicated port instead of the default 22 port is widely increase security. In this blog we will understand how to to srtup SFTP on dedicated port, and inhance security to reduce risk of DDoS attacks on port 22 via ssh.
Why Port 22 Is a Target?
As we all know, port 22 is a default port for the OpenSSH service, which can access any server via the internet. In so many organizations or reputed banks, port 22 is by default changed to some other port to prevent security. This process breaks the shortcut for hackers to hack machines or unnecessary connections generated by them.
Why Use a Dedicated SFTP Port?
- It reduced visibility and security-related issues for port 22, preventing whitelisting for any unauthorized person or organization.
- It is easy to maintain logging for an SFTP server to keep track of records for logged in users.
- Dedicated config to maintain only SFTP service.
How to Setup SFTP on a Dedicated Port?
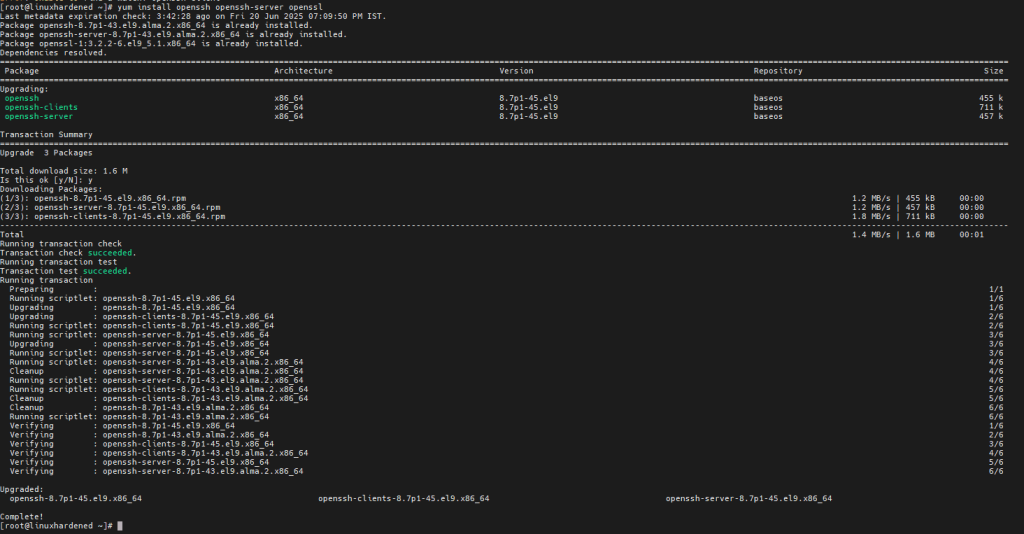
1. Install or update the OpenSSH and OpenSSL services.
Create a Dedicated SFTP User and Directory Structure.
You have to restrict users home directory using chroot method the detailed information is already mentioned about SFTP user creation in previous article.
Configure SFTP config.
After installing openssh and openssl you need to setup some basic steps to setup dedicated port for sftp service.
- Backup and Create Custom Config: cp /etc/ssh/sshd_config /etc/ssh/sftp_config
- Edit Custom SFTP Config (/etc/ssh/sftp_config):
- Set PasswordAuthentication yes (or no if using keys).
- Set PermitRootLogin no.
- Define your dedicated SFTP port: Port 2002 (replace 2002 with your chosen port).
- Set SyslogFacility LOCAL5 and LogLevel VERBOSE for logging.
- Configure SFTP subsystem: Subsystem sftp internal-sftp -l VERBOSE -f LOCAL3
- Define user-specific settings:
- Match user sftpuser (replace sftpuser with actual username)
- ChrootDirectory /sftp/sftpuser (set user’s restricted directory)
- ForceCommand internal-sftp
- Restrict allowed users: AllowUsers sftpuser
[root@linuxhardened ~]# cat /etc/ssh/sftp_config Include /etc/ssh/sshd_config.d/*.conf
Port 2002
SyslogFacility LOCAL5 LogLevel VERBOSE
PermitRootLogin no
MaxSessions 5
AuthorizedKeysFile .ssh/authorized_keys
PasswordAuthentication yes
Subsystem sftp internal-sftp -l VERBOSE -f LOCAL3
UsePAM yes
Banner /etc/issue
Match user sftpuser
ChrootDirectory /sftp/sftpuser
ForceCommand internal-sftp AllowUsers sftpuser
[root@linuxhardened ~]# Create dedicated systemd for sftp.
When using the sshd service, the systemd service will always use the default conf of the sshd service, so you will need to configure another systemd file that makes it easier to manage the SFTP service.
Some simple steps to create it:
Create new .service file in /usr/lib/systemd/system/sftpd.service
Add the below configuration in that file:
# /etc/systemd/system/sftp-server.service
[Unit]
Description=SFTP-only SSH Daemon
After=network.target
Wants=sshd-keygen.target
[Service]
Type=notify
ExecStart=/usr/sbin/sshd -D -f /etc/ssh/sftp_config
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process Restart=on-failure
RestartSec=42s
[Install]
WantedBy=multi-user.targetNow reload the systemd daemon and start the service.
- systemctl daemon-reload
- systemctl start sftp-server.service
After successfully starting the service, check if your custom port is LISTEN or not:
[root@linuxhardened ~]# netstat -tunlp | grep 2002
tcp 0 0 0.0.0.0:2002 0.0.0.0:* LISTEN 94330/sshd: /usr/sb
tcp6 0 0 :::2002 :::* LISTEN 94330/sshd: /usr/sbAfter successfully configuring your SFTP on a dedicated port, you can get ready to go with SFTP user configurations and set up SFTP clients.
While connecting SFTP via client-side, it is always required to mention the port number, which is defined in the file sftpd_config .
NOTE: While using a dedicated port for SFTP, you are required to whitelist the port that is in the LISTEN state.
Security enhancements:
- Use a dedicated IP address to enhance security to isolate SFTP access from other networks on the machine.
- Use rate limits or the fail2ban service, which blocks suspicious login attempts.
- Use key-based authentication in place of passwords to stop unwanted SFTP or SSH daemon login attempts.